Denial Of Service Protection

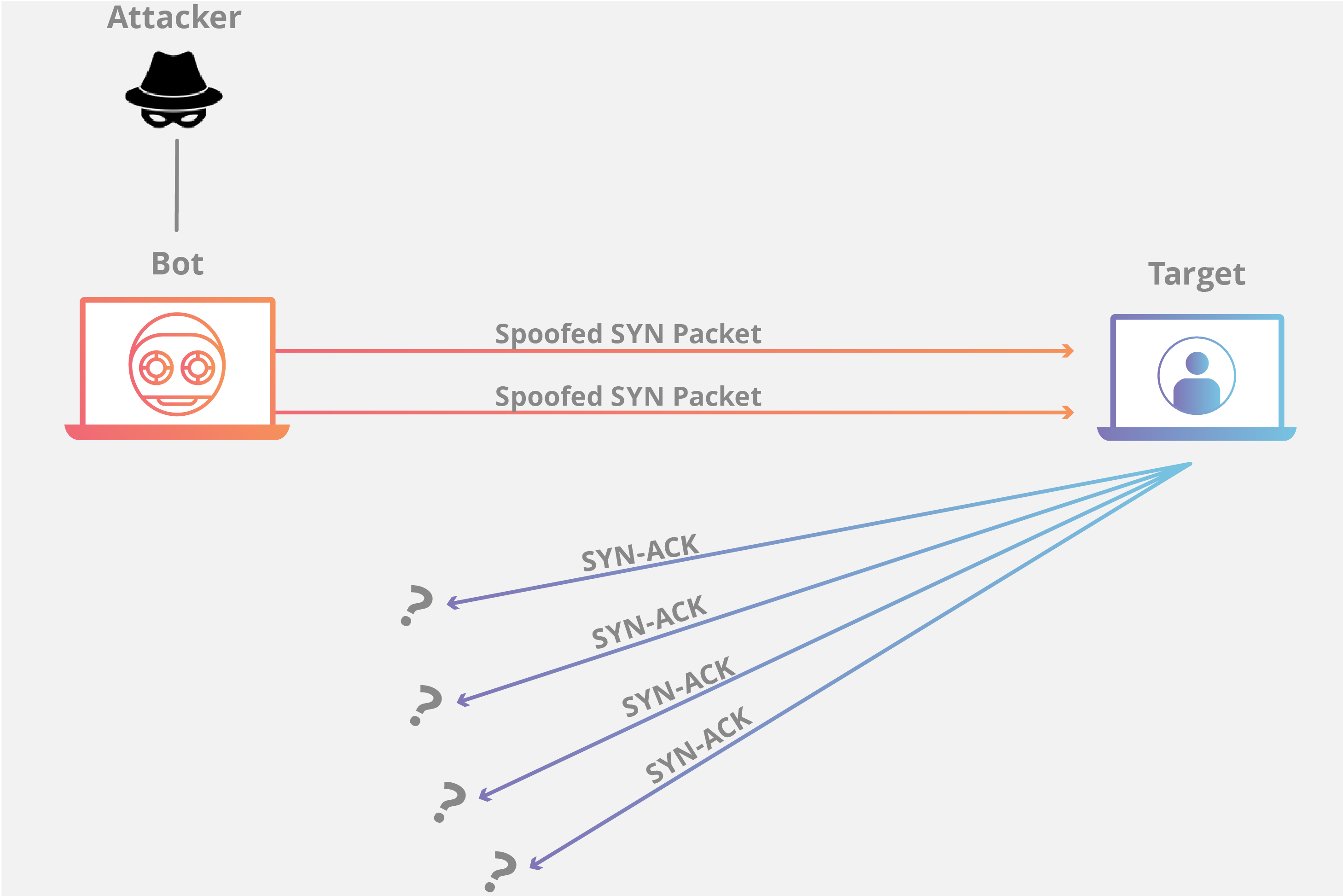
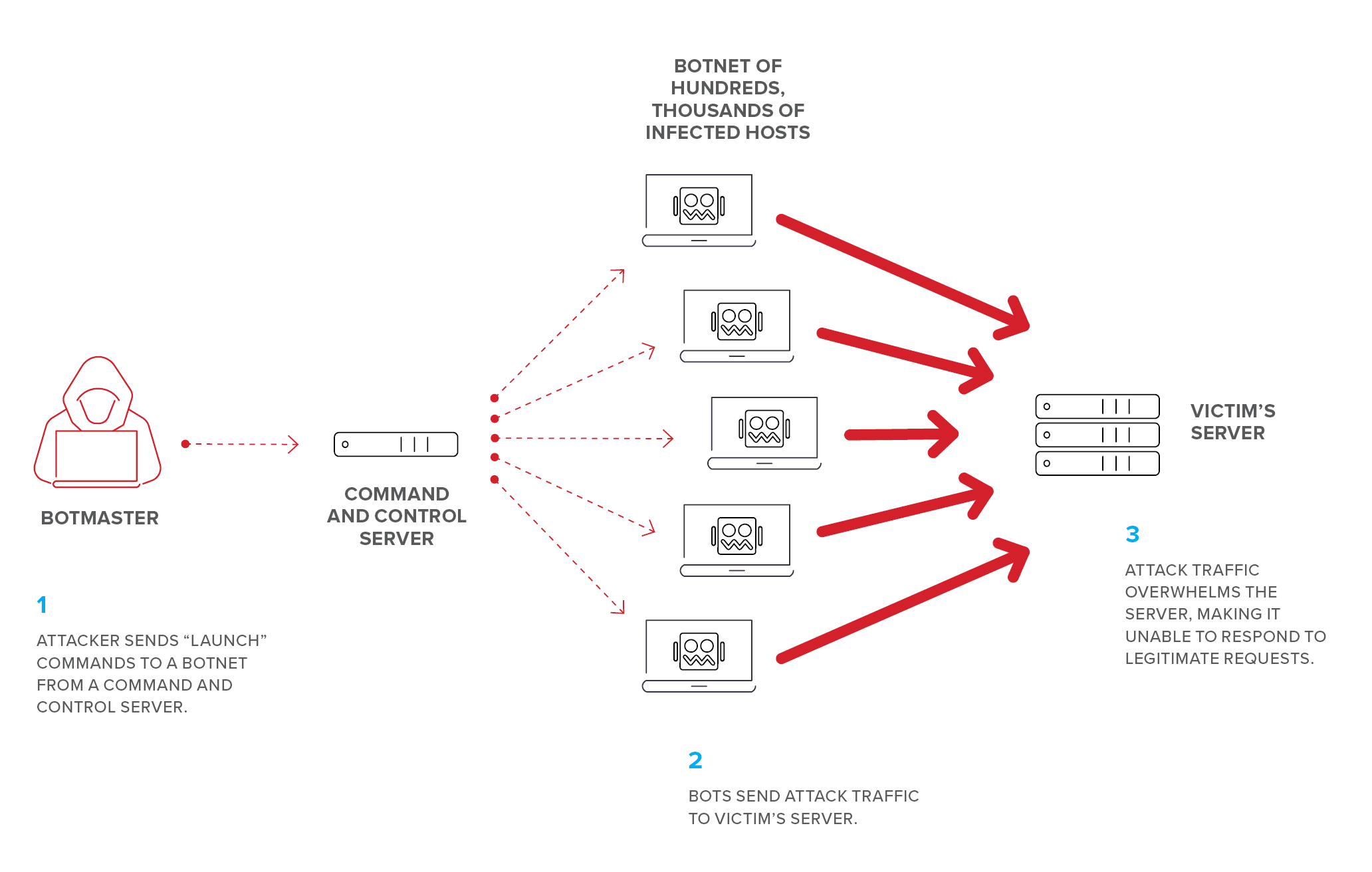
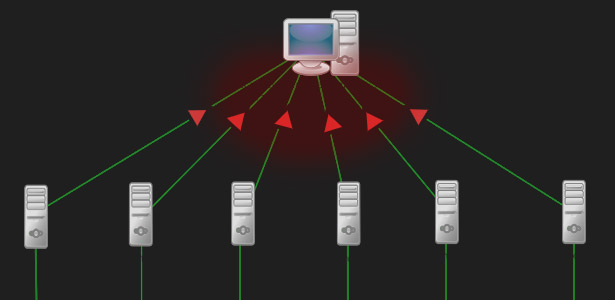
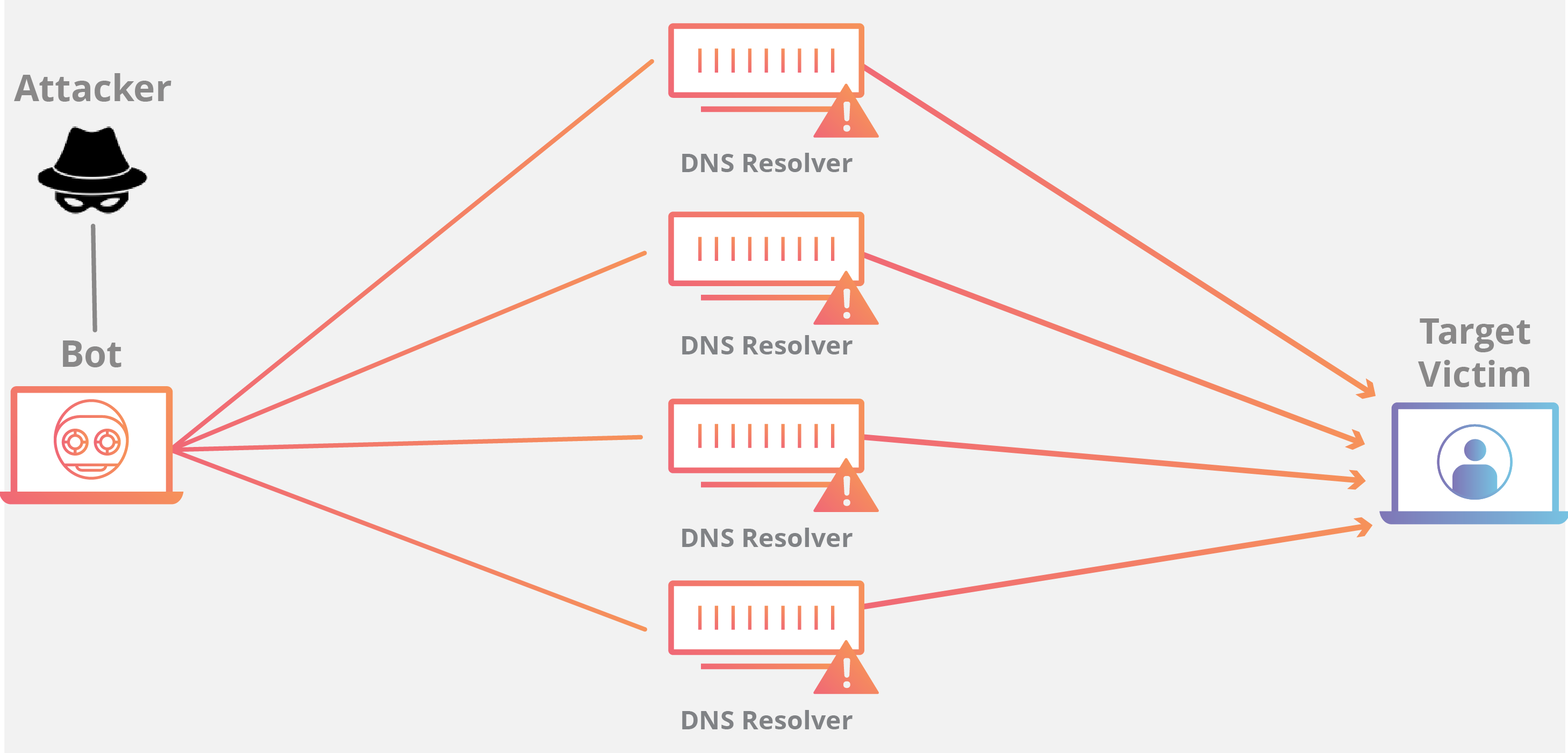
Typically attackers generate large volumes of packets or requests ultimately overwhelming the target system.
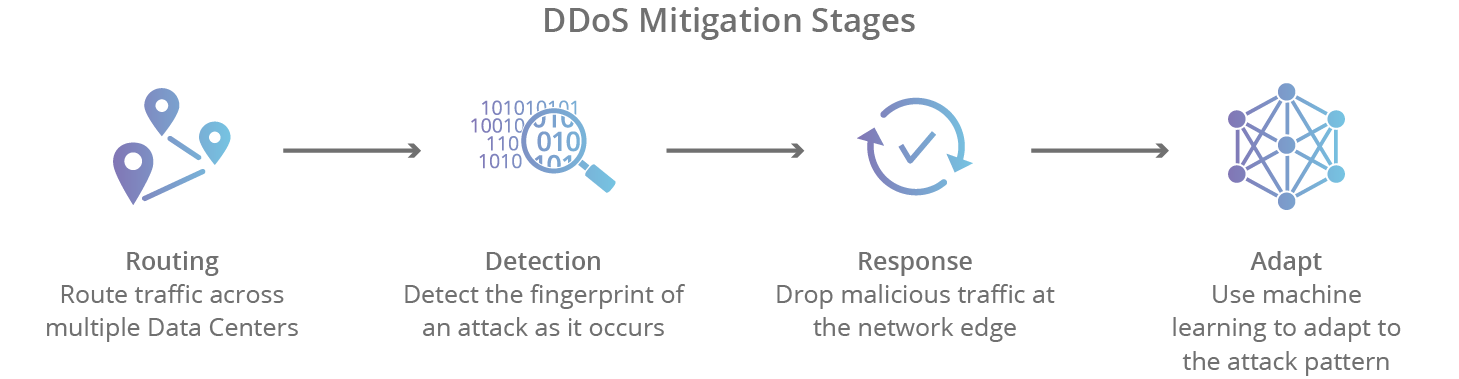
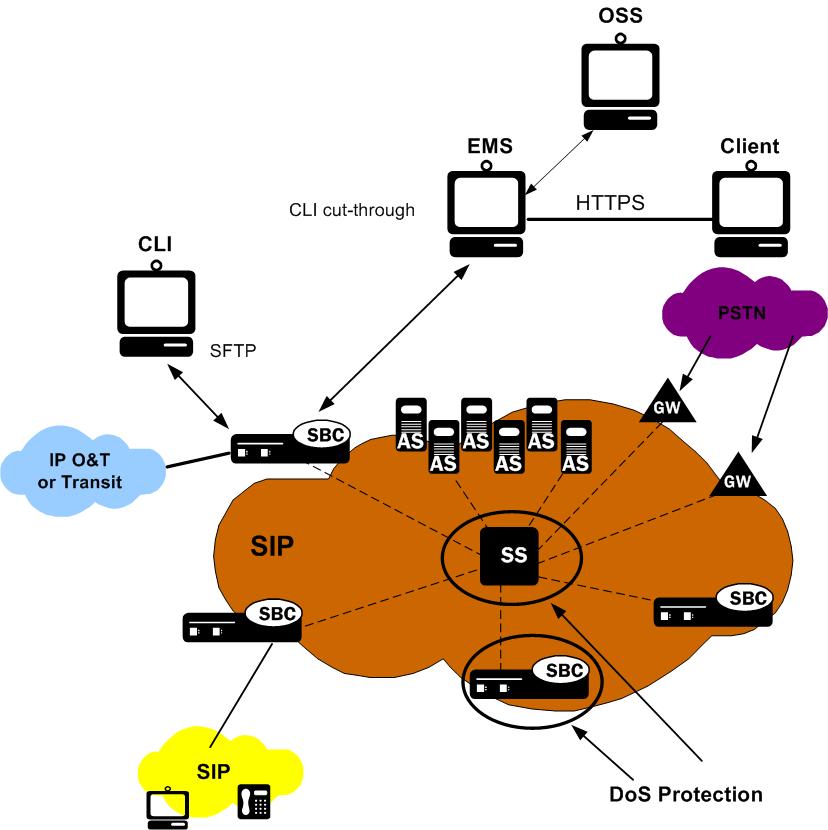
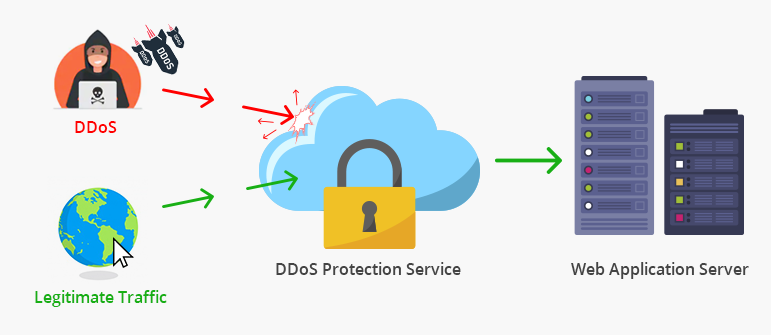
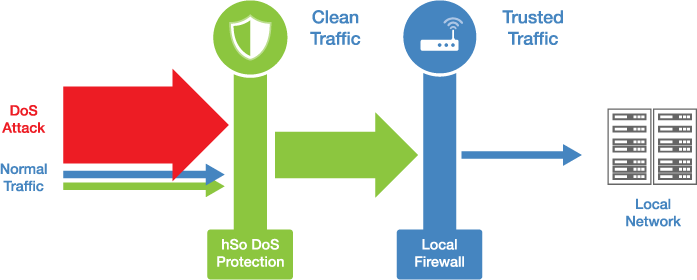
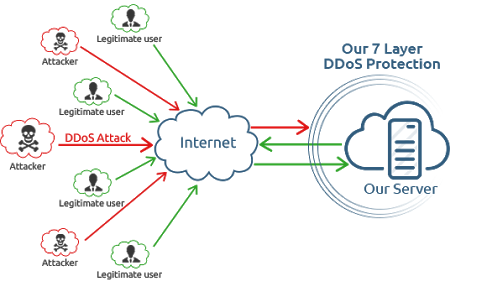
Denial of service protection. For example boundary protection devices can filter certain types of packets to protect information system components on internal organizational networks from being directly affected by denial of service attacks. Distributed denial of service ddos attacks are some of the largest availability and security concerns facing customers that are moving their applications to the cloud. These attacks called distributed denial of service attacks or ddos attacks can often be intense involving hundreds of thousands of computers all over the world and huge amounts of traffic. Amazon s shield protection service says that it successfully defended against the biggest distributed denial of service ddos attack ever recorded.
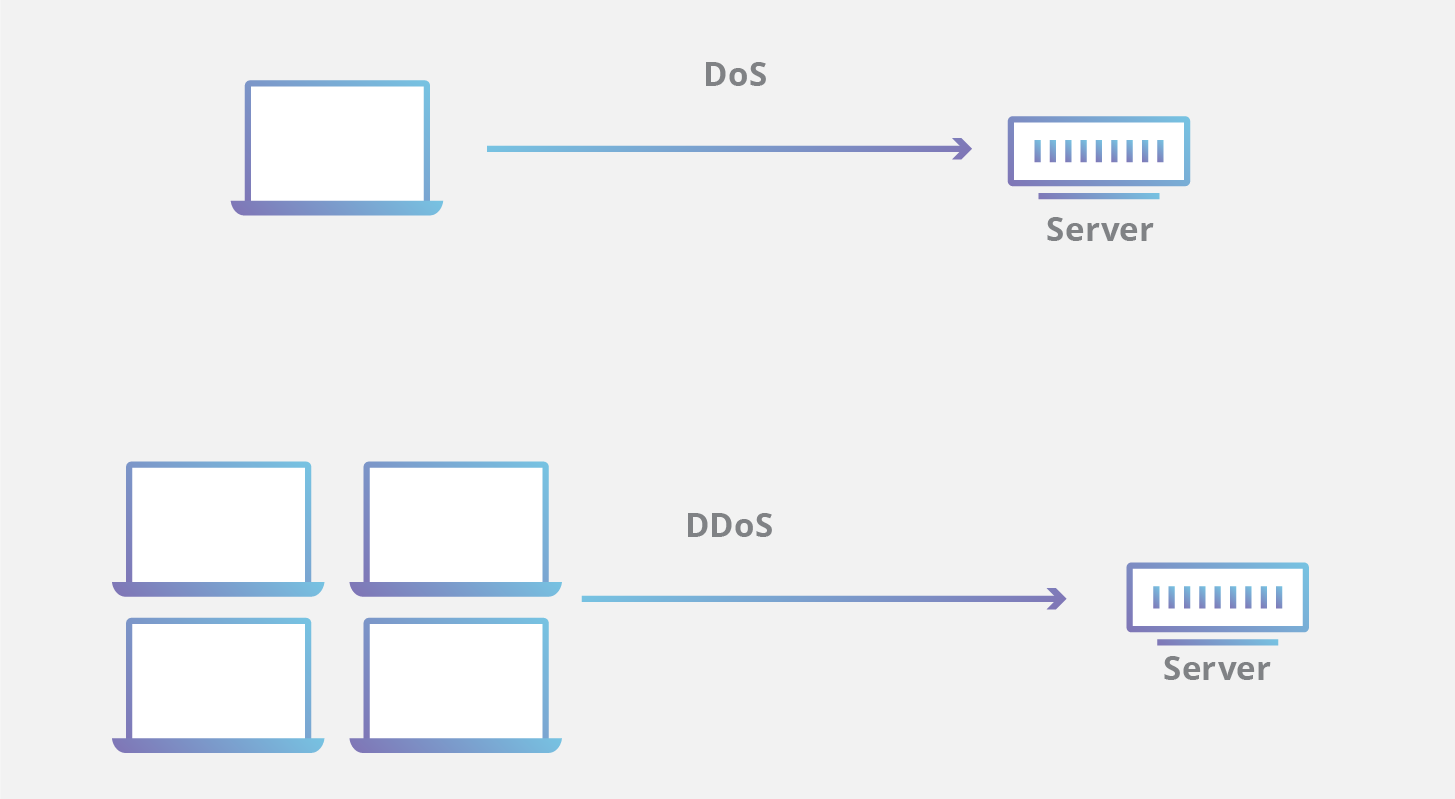
A denial of service dos attack is a type of cyber attack in which a malicious actor aims to render a computer or other device unavailable to its intended users by interrupting the device s normal functioning. 5 minutes to read 10. Distributed denial of service ddos attacks can cripple an organization a network or even an entire country. A denial of service dos attack is a malicious attempt to affect the availability of a targeted system such as a website or application to legitimate end users.
Aws shield is a managed distributed denial of service ddos protection service that safeguards applications running on aws. In computing a denial of service attack dos attack is a cyber attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the internet denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to. Broadly speaking denial of service attacks are launched using homebrewed scripts or dos tools e g low orbit ion canon while ddos attacks are launched from botnets large clusters of connected devices e g cellphones pcs or routers infected with malware that allows remote control by an attacker. Azure ddos protection standard overview.


.png)